Fraud grabbed the global headlines this week, and security professionals were shaking in their respective boots. How would you react to this one: “Massive ransomware infection hits computers in 99 countries”? Within days, 99 soon became 150. Over 300,000 computers were attacked in one all-out assault, as if to insinuate that no man, woman, child, or respected institution could escape the long tentacles of today’s modern cyber-crime syndicate. Yes, the criminal element of our society is highly organized, well resourced, and adept users of the latest technology to achieve their nefarious goals.
Were you a victim? Was your employer on the ropes or at least warning you to pay attention to the latest fraud warning because it was for real? Ransomware is the latest threat on the fraud horizon to gain enormous traction across the globe, as a surefire way to monetize private identity information that has been obtained through rather clever and unscrupulous means. We have written about this phenomenon in previous articles, but never before has an attack been so global in its roll out, as the WannaCry virus.
The attack suggests that there may be a rogue group at the helm, since wise crooks respect the wisdom of staying below the radar screen in most cases. The idea is to milk the public, not cause a large silhouette that law enforcement can easily corral within their constrained budgets. In this case, the early warning signs point to North Korea, a signal that hackers in that country were eager to put the world on notice and impress their young, arrogant ruler. Whatever the case, this attack is not a joke. Everyone is at risk!
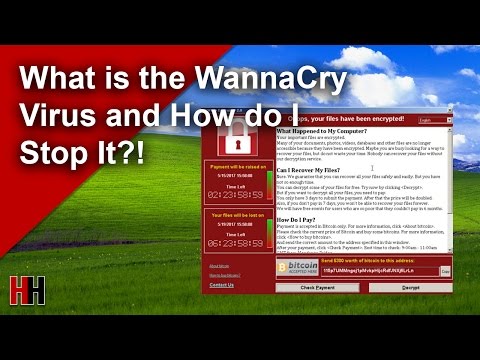
What is the WannaCry virus and why should we be so worried?
We have written extensively about the threat of ransomware attacks. According to security experts, “Ransomware has spread with terrifying speed. This type of malware—short for “malicious software”—accounted for fewer than 2% of emails with malicious links or attachments in the fall of 2015, according to PhishMe, a cybersecurity firm. By last fall, ransomware’s share had zoomed to a shocking 97%. Total ransomware losses in the U.S. hit $1 billion in 2016, up from $24 million in 2015, the FBI estimated.” We added the clarification that, “The FBI has clarified that these estimates are for total implied losses, not “reported losses”, which can be significantly less.”
Bill Conner, President and CEO of SonicWall, added these sobering thoughts: “Ransomware is on the rise. We saw that attacks grew 167 times over, from 4 million in 2015 to 638 million in 2016. Victims typically download ransomware by opening an infected email attachment or clicking a compromised pop-up, triggering malicious code. From there, a sequence of events unfolds that locks down the victim’s device and displays a message listing demands that must be met in order to regain access. In the first quarter of 2016, companies paid an estimated $209 million in ransom, and the number of attacks grew from 30 million to over 260 million by the fourth quarter.”
What makes “WannaCry” so different? Again, from the experts: “Once inside the system WannaCry ransomware creates encrypted copies of specific file types before deleting the originals, leaving the victims with the encrypted copies, which can’t be accessed without a decryption key. WannaCry changes the computer’s wallpaper with messages asking the victim to download the ransomware from Dropbox before demanding hundreds in Bitcoin to work. WannaCry additionally increases the ransom amount, and threatens loss of data, at a predetermined time, creating a sense of urgency and greatly improving the chances victims will pay the ransom.”
The following diagram drives home the maliciousness of this malware variant:
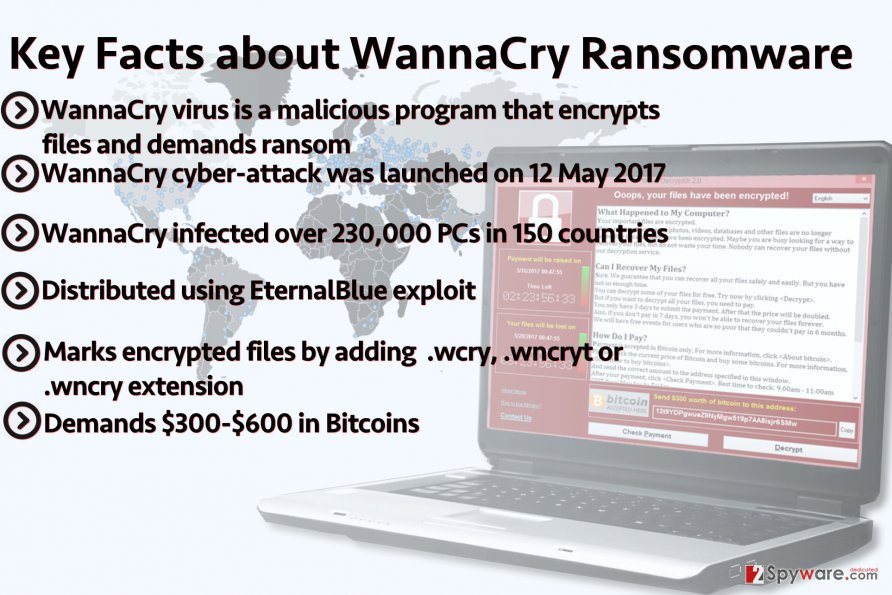
Depending upon the estimation process used, the number of computing devices that have been affected to date could be well beyond current estimates, far removed from the 230,000 shown above and the 300,000 figure cited earlier. The real numbers are off the charts, no matter what security professional is opining upon the subject matter. Consumers in previous attacks have, on average, been bilked for a conservative amount of $250, but hospitals, banks, large data processing aggregators, brokers, and even government entities have been know to pay upwards of $250,000 to get back online and not miss a beat when supporting their proprietary databases of customers.
What can be said about the origin of this hideous assault on public providers?
Believe it or not, security professional have a forensic method for determining who is at the bottom of these criminal activities. Once again, organized crime would not attempt to pull off such a high profile stunt to earn its wages of sin. That band of thieves would want to keep a low profile, avoid law enforcement at every turn, and then turn the faucet on ever so slightly, such that a steady stream of ill-gotten gains poured into their coffers. Crooks prefer the long-term approach. There is no benefit to constructing a big, grand hit, if you know you will be shut down in hours.
So who was responsible? Experts find that the lines of code tell the story. The unmistakable signature of the Lazurus Group suggests that the attack originated in North Korea. The prevailing theme from each investigative perspective reads as follows:
“The Lazarus hackers have been linked to North Korea, raising suspicions that the nation could be responsible for the attack. The connection was made by Google security researcher Neel Mehta, who pointed out similarities between WannaCry and malware used by Lazarus, the group that has been blamed for the Sony Pictures hack of 2014 and for stealing millions of dollars from a Bangladeshi bank in 2016. Other researchers confirmed similarities that early versions of WannaCry — also called WannaCrypt, Wana Decryptor or WCry — shared with malware tools used by Lazarus.”
Regardless of the source, it is a fairly serious allegation to claim that an independent nation state is actually exploiting the use of ransomware to further its aims and ambitions. Not everyone is willing to jump to this conclusion, although quite a few of the early victims were South Korean concerns. Per one report: “At least 12 South Korean companies have been hit by the WannaCry computer virus. It has disrupted ads for a local theater chain, and bus schedules in a small city south of the capital Seoul. But South Korea doesn’t appear to be hurt any more than other countries.”
Where were the other large initial hits? Headlines were quick to focus on attacks of the national health system for the UK and for Spain’s largest telecom company, but oddly missing from the initial barrages were notations for U.S. companies. Needless to say, White House homeland security adviser, Tom Bossert, quickly noted that, “The WannaCry cyberattack has hit more than 300,000 computers. While U.S. investigators don’t know who is responsible for WannaCry, there are clues to follow.” It goes without saying that this broadside is the largest single coordinated cyber-attack in history. Who cares where it came from? How do we stop it and protect ourselves?
What are a few tips for both detection and prevention?
The response from security professionals and IT specialists has been enormous. The Lazerus Group or whoever is causing this mayhem is exploiting a “coding hole” within the Microsoft software operating system. Detection and prevention then become paramount, but nearly everyone advises victims not to pay the ransom. Yes, a few victims may have had no choice, but in those cases, the decryption key has not been forthcoming. You can waste your money, go down on a list of individuals and companies that are willing to pay, but at the end of the day, your files will remain encrypted.
Here are a few suggestions on the detection front – be wary of the fraudsters if they:
- Create a sense of urgency on your part. This is typically in the form of a threat. If you don’t respond your account will be disabled. A threat may also be a financial one, or one involving your reputation.
- Ask for information the sender should already have or shouldn’t ask for. For instance you financial institution sending you an email to confirm your account number, Credit Card Number, login ID etc…
- Send you an email from a government institution with a financial threat, such as, the IRS sending an email about back taxes. Law enforcement fake emails may suggest that you are under investigation.
- Send a shipping notification from UPS or Fedex stating delivery failure.
- Use grammar that is not quite right, subject and verb tense don’t match, or words are misspelled.
- The greeting is very generic.
It is easy to fall victim at this stage. Crooks are very adept at playing upon your emotions. Your first course of preventative action should be to protect your home network from compromise. Request a “patch” from Microsoft. They have websites responding to these requests at this time. Here are a few other tips:
- When you look at the email does it cause you to become anxious? Trust your gut instinct and delete it.
- In the case of a known contact sending you an email, does the email sound like something the sender would send you?
- When you receive an email that contains information about a legitimate company and you want to verify the legitimacy, do not use any information in the suspect email. Open a web browser and find the legitimate company’s web site. Somewhere on that page, typically in small print at the bottom, will be a way to contact the company. We suggest you call their customer service number.
- If you receive an email that appears to come from your employer, call your IT helpdesk to verify the legitimacy of the correspondence.
- If you receive a shipping notification failure, are you expecting a delivery? Did you use the email address that appeared in the non-delivery email when you made the order? If the answer is no for either of these questions, the email is fake.
- Government entities do not contact you via email. The IRS sends tax notifications via the Post Office. The same is true for Microsoft. Large software entities would never call you directly by phone.
- Law enforcement doesn’t give you a heads-up by phone. They typically just come knock on your door.
Concluding Remarks
The WannaCry ransomware threat is real, and its perpetrators have reached out to every corner of the globe to defraud companies and individuals with impunity. The time is now to get a protective “patch” from Microsoft. Stay extremely vigilant at all times!
Related Articles
- Forex vs Crypto: What’s Better For Beginner Traders?
- Three Great Technical Analysis Tools for Forex Trading
- What Does Binance Being Kicked Out of Belgium Mean for Crypto Prices?
- Crypto Traders and Coin Prices Face New Challenge as Binance Gives up its FCA Licence
- Interpol Declares Investment Scams “Serious and Imminent Threat”
- Annual UK Fraud Audit Reveals Scam Hot-Spots
Forex vs Crypto: What’s Better For Beginner Traders?
Three Great Technical Analysis Tools for Forex Trading
Safest Forex Brokers 2025
| Broker | Info | Best In | Customer Satisfaction Score | ||
|---|---|---|---|---|---|
| #1 |
|
Global Forex Broker |

BEST SPREADS
Visit broker
|
||
| #2 |
|
Globally regulated broker |

BEST CUSTOMER SUPPORT
Visit broker
|
||
| #3 |
|
Global CFD Provider |

Best Trading App
Visit broker
|
||
| #4 |
|
Global Forex Broker |

Low minimum deposit
Visit broker
|
||
| #5 |
|
Global CFD & FX Broker (*Don’t invest unless you’re prepared to lose all the money you invest. This is a high-risk investment and you should not expect to be protected if something goes wrong. Take 2 mins to learn more) |

ALL-INCLUSIVE TRADING PLATFORM
Visit broker
|
||
| #6 |
|
Global Forex Broker |

Low minimum deposit
Visit broker
|
||
| #7 |
|
CFD and Cryptocurrency Broker |

CFD and Cryptocurrency
Visit broker
|
||
|
|
|||||
Forex Fraud Certified Brokers
Stay up to date with the latest Forex scam alerts
Sign up to receive our up-to-date broker reviews, new fraud warnings and special offers direct to your inbox


